The Problem
Static code analysis is a technology to detect various security vulnerabilities at implementation time. However, as studies show, developers reject static analysis tools, as they find them hard to configure such that they can operate efficiently in their application context. With their default parameters, most tools produce a high number of false warnings, while missing vulnerabilities that may be important. This demotivates the developers. The goal of this project is to reduce the gap between static analysis and software development, thereby improving the user experience of static analysis tools.
Security by design principles expect that developers can check their own code against security vulnerabilities before they push the code into production. Therefore, static analysis tools that are integrated in the developer’s IDEs can be of a great use. They help developers during development time to fix many security vulnerabilities. However, most of these tools are in early research phase and not mature enough to be used in practice.
To what extent can we reduce the gap between the domains of static analysis and software development? Within this project, we work on an approach for the automatic generation of security checkers based on vulnerability specifications. The project focuses on the detection of Java vulnerabilities.
Our Solution: SecuCheck
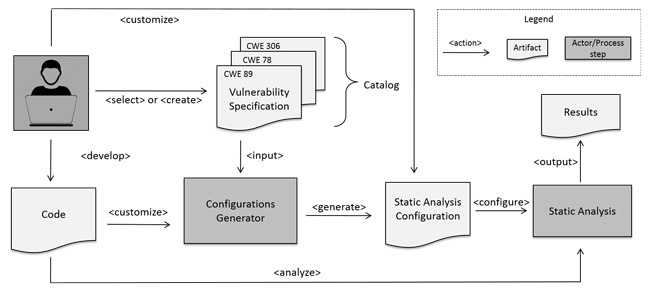
The vulnerability specification and the program code are the inputs that a developer needs to provide to the generator of security checkers. The generator takes the vulnerability specification and produces a parameterized analysis for the user’s program code. We call this a security checker. For example, a developer selects a specification for SQL injection and wants to check a given code. The generator will execute the following steps :
- select the appropriate static analysis, which in this example will be a taint analysis,
- scan the code to infer the specific information, for example find the relevant methods, like sources, sinks and sanitizers, required for taint analysis,
- parameterize the analysis (select call graph algorithm, choose forward or backward analysis, etc.),
- run the analysis and
- display the results.
